Binary (pwn) challenges
For each task two binaries are available. One can be downloaded for the local analysis (debugging, exploitation). The task is to write the exploit for the binary that opens a shell for command execution. The remote copy of the binary is running on the indicated server. Exploiting the remote binary, the flag can be obtained e.g. cat flag.txt.
Stack overflow
Stack overflow 1.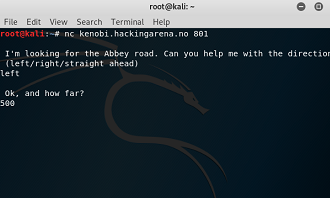 local binary: abbey remote binary: kenobi.hackingarena.no:801 |
Stack overflow 2.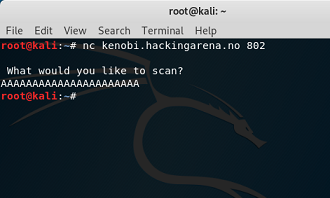 local binary: scanner remote binary: kenobi.hackingarena.no:802 |
Stack overflow 3.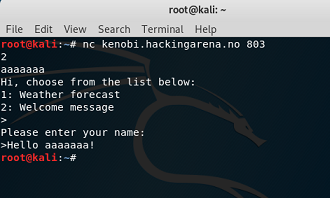 local binary: options remote binary: kenobi.hackingarena.no:803 |
Stack overflow 4.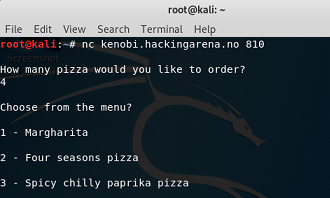 local binary: summerpizza remote binary: kenobi.hackingarena.no:810 |
Return Oriented Programming (ROP)
ROP 1.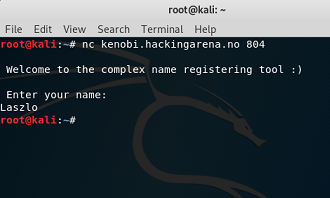 local binary: getnameROP remote binary: kenobi.hackingarena.no:804 |
ROP 2.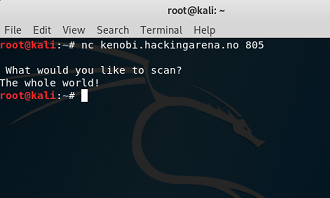 local binary: scannerROP remote binary: kenobi.hackingarena.no:805 |
ROP 3.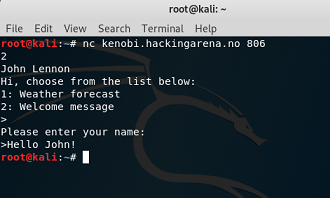 local binary: optionsROP remote binary: kenobi.hackingarena.no:806 |
ROP 4.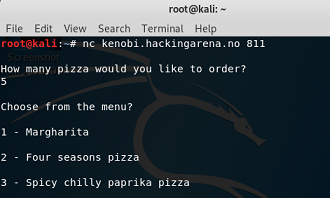 local binary: summerpizza2 remote binary: kenobi.hackingarena.no:811 |
Heap vulnerabilities
Heap 1.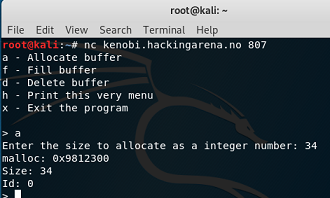 local binary: fastbintostack remote binary: kenobi.hackingarena.no:807 |
Heap 2.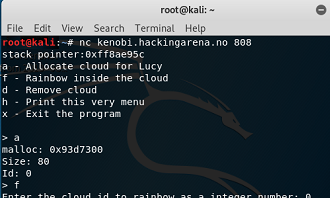 local binary: lucysky remote binary: kenobi.hackingarena.no:808 |
Heap 3.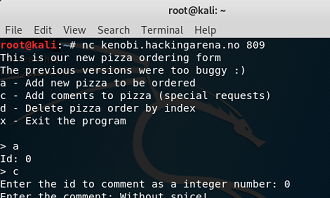 local binary: pizzaheap remote binary: kenobi.hackingarena.no:809 |